
by DTS Staff | Blog
When we think about the things that can stop a business dead in it’s tracks, our minds go to different things. Some may think of a lack of inventory. Recently we have seen problems due to a lack of employees. Others worry about being obsolete in the marketplace, like...

by DTS Staff | Blog
We don’t have private lives anymore. While to many of us, including this writer, it’s unfortunate, it’s the truth of the modern times we live in. Social media has been with us since the early 2000’s with Myspace, but it has become increasingly prevalent in our lives...

by DTS Staff | Blog
Have you ever ignored emails from potential leads because you were nervous that they could be fake or malicious? In today’s world, we are taught to be skeptical of what crosses our inbox. Cyberthreats come masked in the form of trusted brands and lure users into...

by DTS Staff | Blog
Take a second and look around your house. I am sure you see appliances abound, but do you see a phone? Not a cellphone or a tablet, but an actual hardwired landline. Chances are probably not. Now, think about your office. There it is there’s phones everywhere! In...
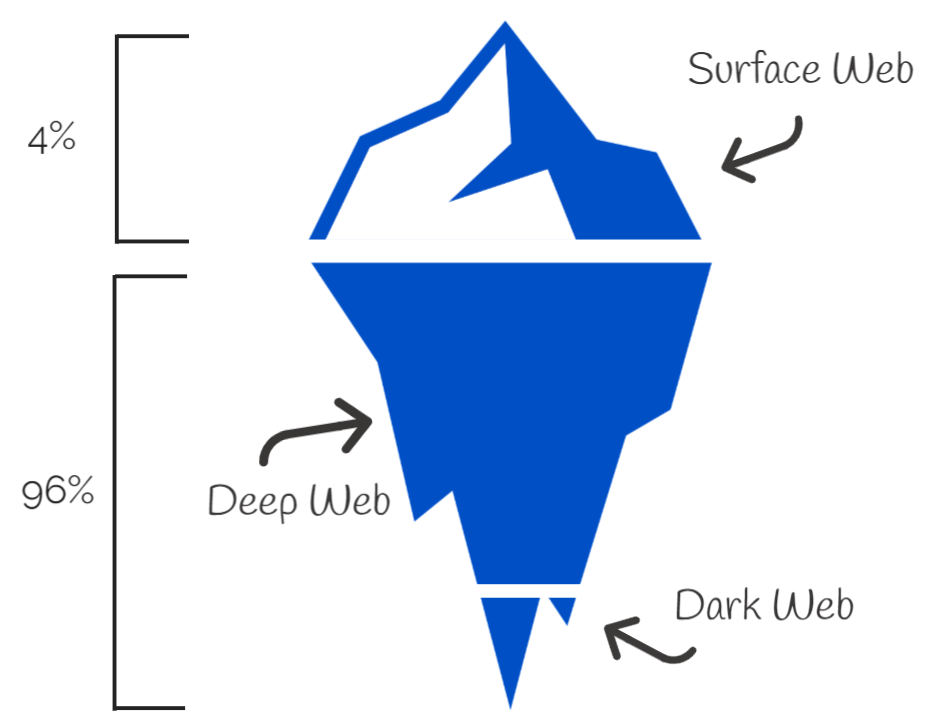
by DTS Staff | Blog
Your Data and The Dark Web At this point daily, you and your team are most likely getting emails, texts and direct messages from people claiming everything from needing a verification on a bank account, that you won a million dollars in a contest you didn’t enter, or...

by DTS Staff | Blog
To be sure that your business is productive, efficient and capable of growth, it’s important to prioritize the health and functionality of your IT infrastructure. This will allow you to keep your critical data safe and your business operations up and running. Even in...






