by DTS Staff | Blog
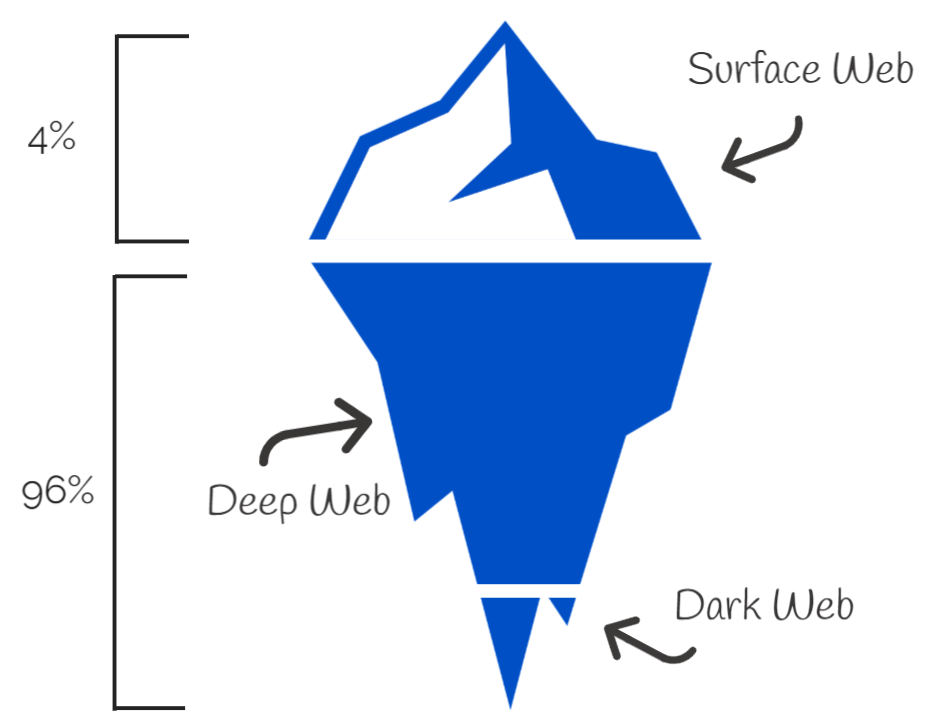
Your Data and The Dark Web At this point daily, you and your team are most likely getting emails, texts and direct messages from people claiming everything from needing a verification on a bank account, that you won a million dollars in a contest you didn’t enter, or...

by DTS Staff | Blog
To be sure that your business is productive, efficient and capable of growth, it’s important to prioritize the health and functionality of your IT infrastructure. This will allow you to keep your critical data safe and your business operations up and running. Even in...

by DTS Staff | Blog
We have all heard the phrase “If it ain’t broke, don’t fix it”. While that is sound advice on certain things that we do in our lives, it also points to a problem many face when it comes to the modern business world. Many of us work on the thought process that the only...
by DTS Staff | Blog
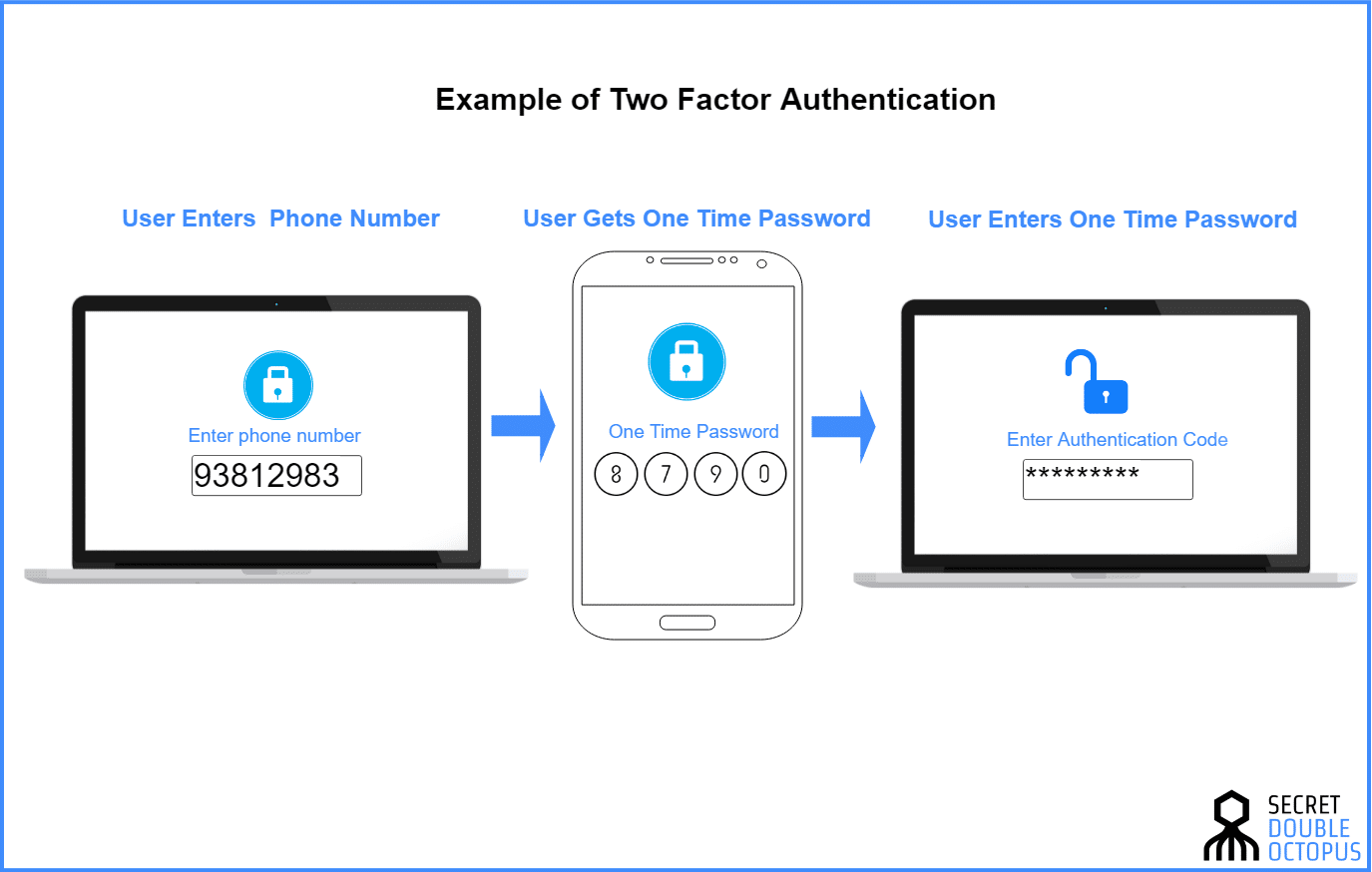
Fluidity has become a hot button issue for business owners. More and more, you need fluid streams of capital, fluid business models, and a fluid workforce, able to work from anywhere they need to, on any device they need to. This past year we as a populace have...
by DTS Staff | Blog
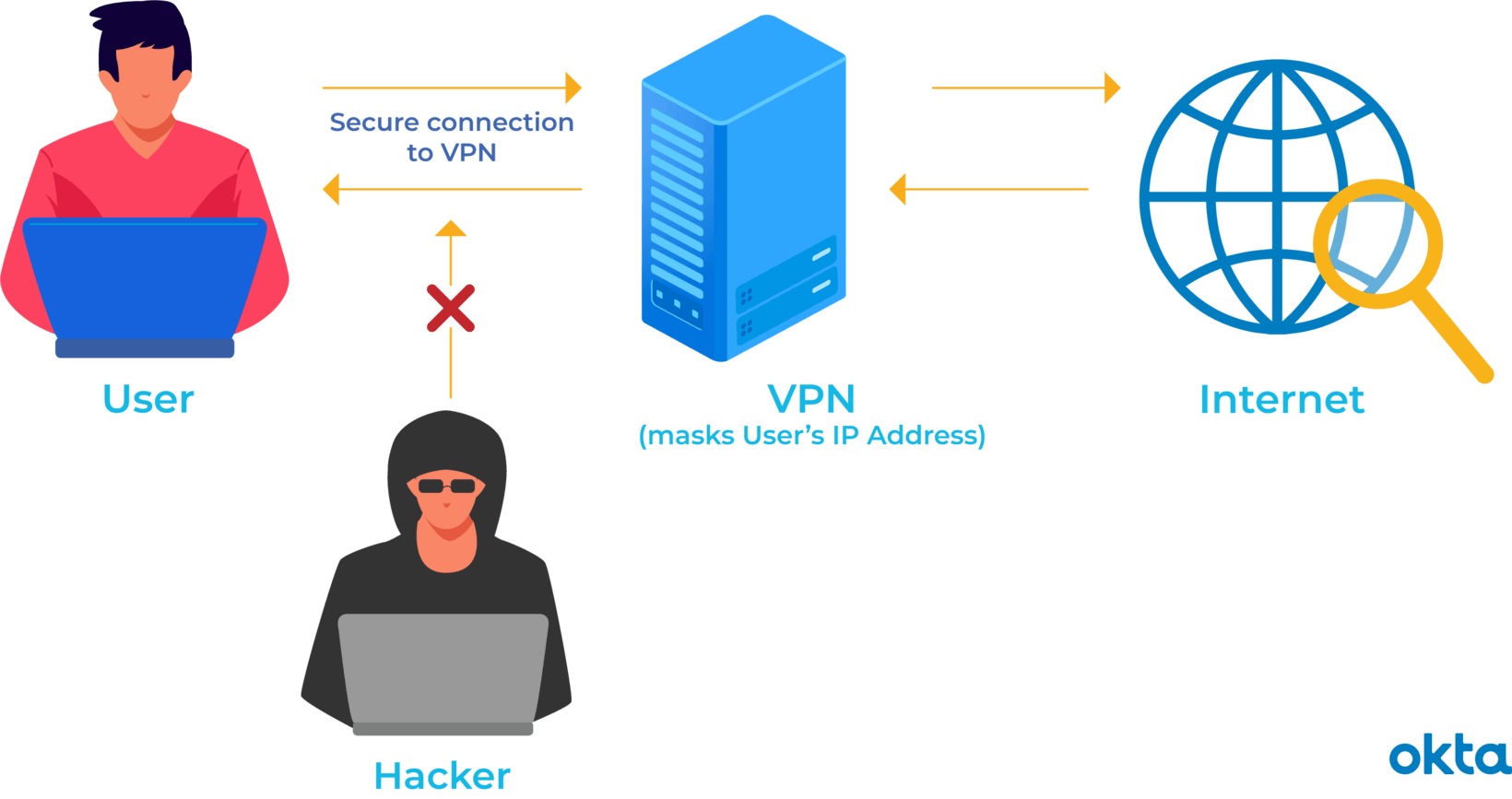
Ralph is a small business owner with a team of 10, most of which are in the field. They work off their phones, tablets and personal laptops from wherever they may be. Ralph has seen that more and more hacking attacking on small businesses are taking place, and knows...





