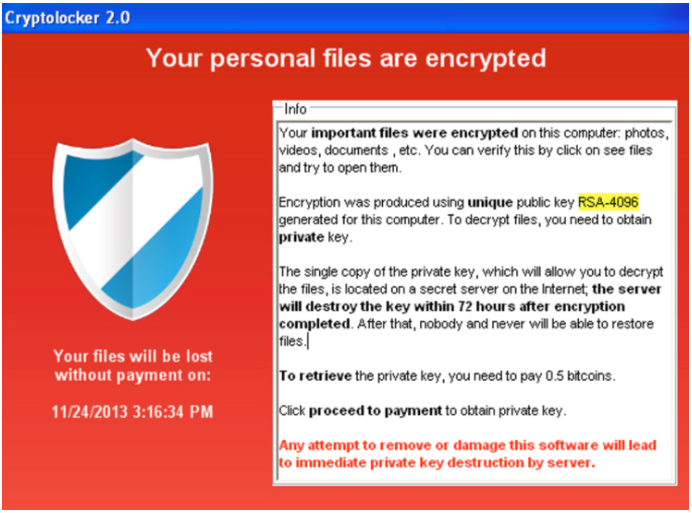
by DTS Staff | Blog
Cyber attacks have been on the rise across the board between 2020 and 2021. In fact this year, there has been a 102% rise in ransomware attacks carried out by hacker. This past week we have seen, and many of us have felt, two major ransomware attacks and their...

by DTS Staff | Blog
Each year, the volume of cybersecurity threats continues to steadily climb, with more than one billion malware programs out there and approximately 560,000 new pieces of malware being detected each day. All the while, regulations, such as the...

by DTS Staff | Blog
It has been said that we live in an era of infinite choice. From the foods you eat, the shows you watch, to the goods you purchase, the possibilities are endless, and at times so is the confusion. Oftentimes our choice comes down to who is providing the service...

by DTS Staff | Blog
2020 and the Covid pandemic not only changed the way a lot of companies do business, but it also changed the way hackers attack those businesses. Last year, cyber attacks were up over 200 percent, and this trend shows no signs of letting up. More people are working...




