Delval Tech Blog
Leading source for news, information & resources for Information Technology

Four Phishing Prevention Strategies Any Business Can Employ
Have you ever ignored emails from potential leads because you were nervous that they could be fake or malicious? In today’s world, we are taught to be skeptical of what crosses our inbox. Cyberthreats come masked in the form of trusted brands and lure users into sharing otherwise secure data. And while being crucial for business operations, email provides attackers with an opportunity to infiltrate your system. So, what can a business do to conduct business efficiently and safely? Here are...

Why VOIP?
Take a second and look around your house. I am sure you see appliances abound, but do you see a phone? Not a cellphone or a tablet, but an actual hardwired landline. Chances are probably not. Now, think about your office. There it is there’s phones everywhere! In fact, businesses are perhaps the last place where we use classic landline phones. Stores, office spaces, garages, warehouses, all full of phones. You already knew that. What you may not have known is this, you do not need a...
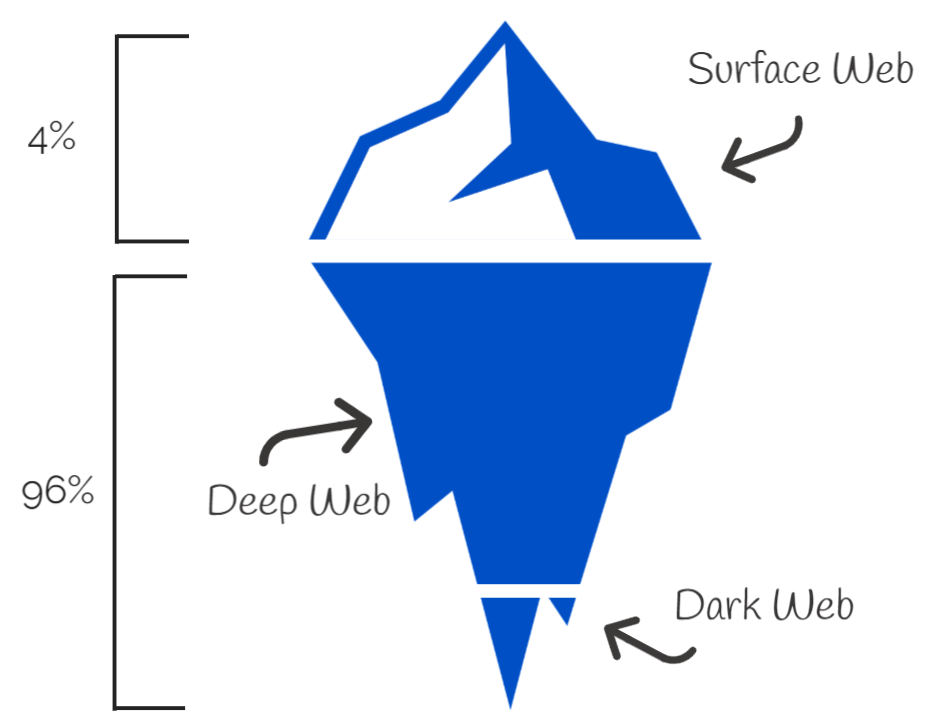
The Dark Web: Where Your Stolen Data is a Commodity
Your Data and The Dark Web At this point daily, you and your team are most likely getting emails, texts and direct messages from people claiming everything from needing a verification on a bank account, that you won a million dollars in a contest you didn’t enter, or HR needs your login credentials, from accounts that aren’t what they seem. These social engineering attacks serve one purpose, to get access to your network and grab your and your client’s information. This could be anything from...

3 Ways Your Business Could Benefit from an IT Consulting Service
To be sure that your business is productive, efficient and capable of growth, it’s important to prioritize the health and functionality of your IT infrastructure. This will allow you to keep your critical data safe and your business operations up and running. Even in the event of disaster, IT consulting increases the productivity and value of your business. That being said, it’s not always easy to prioritize your technology obligations in addition to managing the other day-to-day demands of...

Why The Broke/Fix Method is Broken
We have all heard the phrase “If it ain’t broke, don’t fix it”. While that is sound advice on certain things that we do in our lives, it also points to a problem many face when it comes to the modern business world. Many of us work on the thought process that the only time you need to concern yourself with issues is when something is broken, but that is an antiquated thought process in many aspects of enterprise. Your business IT, computer system and network fall into this category. You need...
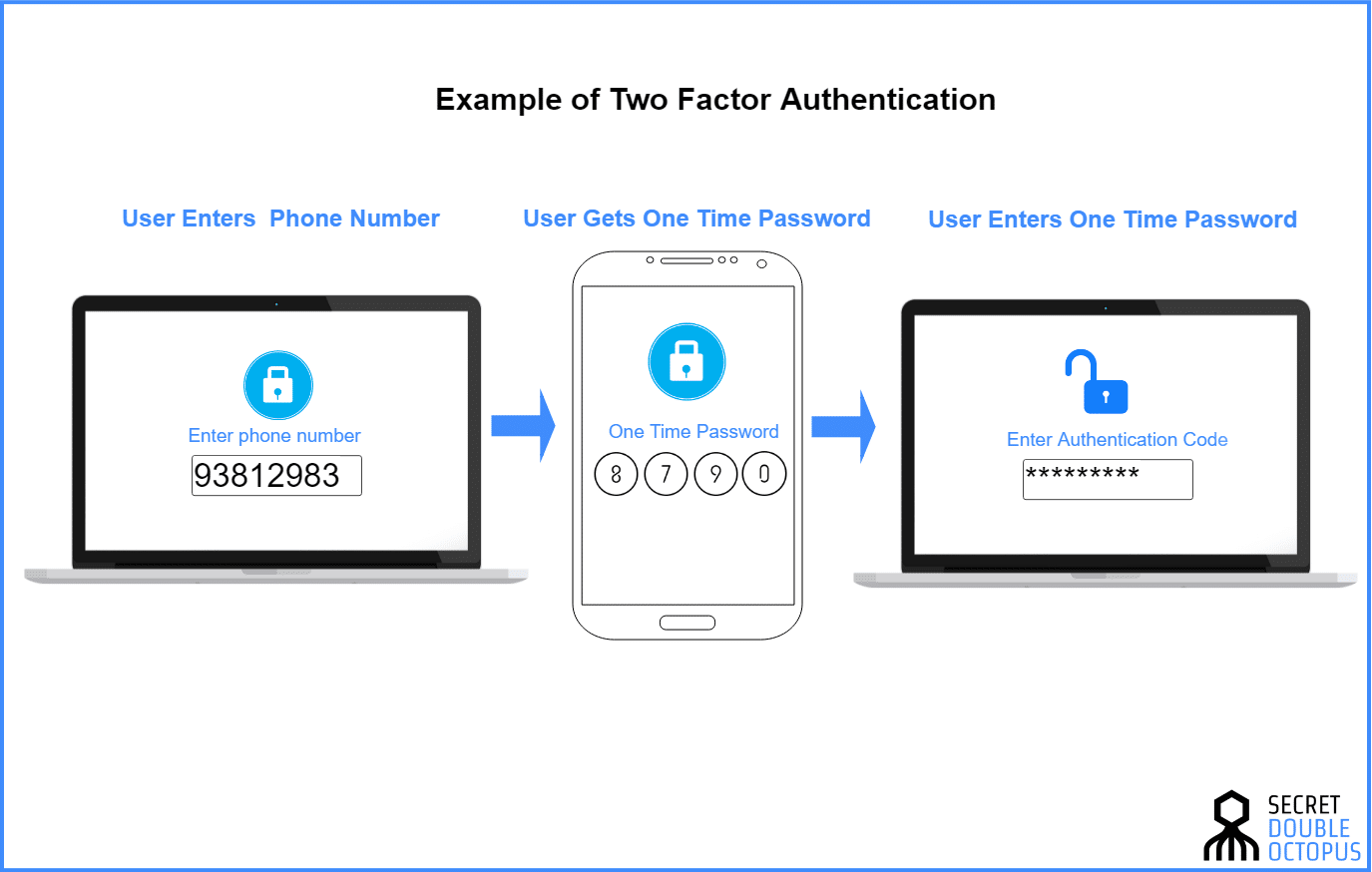
2 Factor Authentication: Can You Afford NOT to Have It?
Fluidity has become a hot button issue for business owners. More and more, you need fluid streams of capital, fluid business models, and a fluid workforce, able to work from anywhere they need to, on any device they need to. This past year we as a populace have witnessed drastic changes occur to our day-to-day work lives, and more importantly, many of us have seen how much more productive this form of working can be for everyone involved. However, with new advances you end up with new issues,...
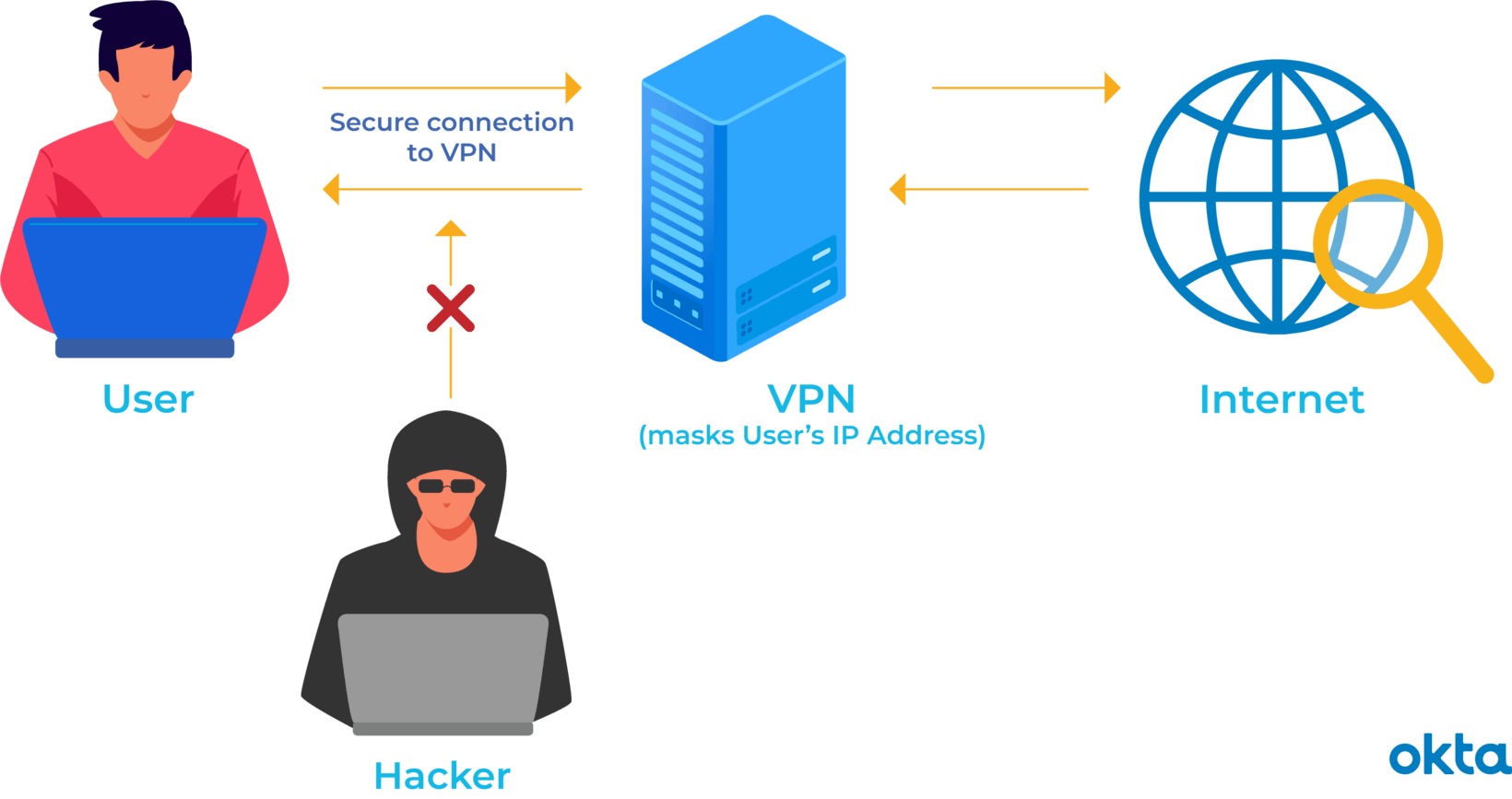
VPN’s and Your Business
Ralph is a small business owner with a team of 10, most of which are in the field. They work off their phones, tablets and personal laptops from wherever they may be. Ralph has seen that more and more hacking attacking on small businesses are taking place, and knows that by his team using public wifi, they are more exposed to these malicious actors. Due to the nature of their work, everything from where they browse, to their write ups, and the files they send to each other are proprietary...

Top Tech Trends for 2021
TOP TECH TRENDS OF 2021 FOR YOUR BUSINESS What a difference a year makes. When it comes to the technology we use for business, innovations come quickly and trends change rapidly. Knowing what’s on the horizon and what to look for can be the difference between being ahead of the curve or being left in the dust to play catch up. In 2020 we dealt with a world changing event. As we come out of it in the second half of 2021, what should you be looking for when it comes to tech? What are some trends...
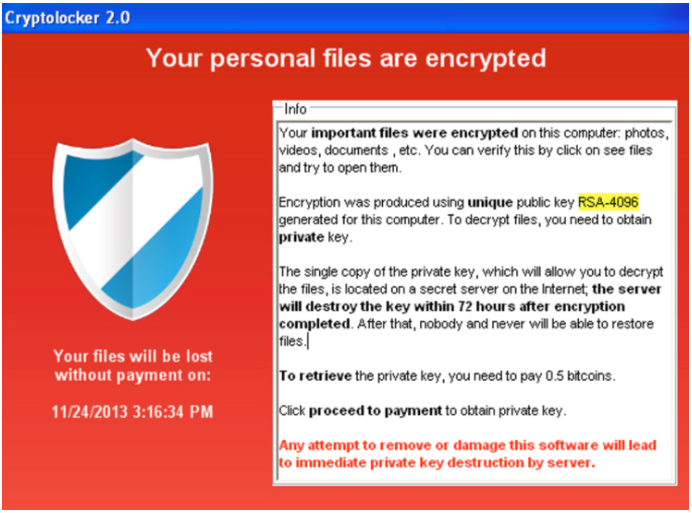
Ransomware, The DC Police & The Colonial Pipeline
Cyber attacks have been on the rise across the board between 2020 and 2021. In fact this year, there has been a 102% rise in ransomware attacks carried out by hacker. This past week we have seen, and many of us have felt, two major ransomware attacks and their fallout. What was once something that was regulated only to businesses and smaller institutions have become big business to hackers, with companies paying out millions of dollars to get there networks back in order and mitigate damages....

How to Take a Proactive Approach to Cybersecurity
Each year, the volume of cybersecurity threats continues to steadily climb, with more than one billion malware programs out there and approximately 560,000 new pieces of malware being detected each day. All the while, regulations, such as the General Data Protection Regulation (GDPR) are constantly evolving. This means even the most minor of security breaches can be incredibly devastating for your organization, leading to negative publicity, hefty fines and a loss of confidence in your brand....